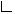 org.apache.shiro.mgt.CachingSecurityManager
org.apache.shiro.mgt.CachingSecurityManager
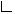 org.apache.shiro.mgt.RealmSecurityManager
org.apache.shiro.mgt.RealmSecurityManager
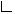 org.apache.shiro.mgt.AuthenticatingSecurityManager
org.apache.shiro.mgt.AuthenticatingSecurityManager
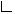 org.apache.shiro.mgt.AuthorizingSecurityManager
org.apache.shiro.mgt.AuthorizingSecurityManager
|
||||||||||
| PREV CLASS NEXT CLASS | FRAMES NO FRAMES | |||||||||
| SUMMARY: NESTED | FIELD | CONSTR | METHOD | DETAIL: FIELD | CONSTR | METHOD | |||||||||
java.lang.Objectorg.apache.shiro.mgt.CachingSecurityManager
org.apache.shiro.mgt.RealmSecurityManager
org.apache.shiro.mgt.AuthenticatingSecurityManager
org.apache.shiro.mgt.AuthorizingSecurityManager
public abstract class AuthorizingSecurityManager
Shiro support of a SecurityManager class hierarchy that delegates all
authorization (access control) operations to a wrapped Authorizer instance. That is,
this class implements all the Authorizer methods in the SecurityManager
interface, but in reality, those methods are merely passthrough calls to the underlying 'real'
Authorizer instance.
All remaining SecurityManager methods not covered by this class or its parents (mostly Session support) are left to be implemented by subclasses.
In keeping with the other classes in this hierarchy and Shiro's desire to minimize configuration whenever possible, suitable default instances for all dependencies will be created upon instantiation.
| Constructor Summary | |
|---|---|
AuthorizingSecurityManager()
Default no-arg constructor that initializes an internal default ModularRealmAuthorizer. |
|
| Method Summary | |
|---|---|
protected void |
afterRealmsSet()
First calls super.afterRealmsSet() and then sets these same Realm objects on this
instance's wrapped Authorizer. |
void |
checkPermission(PrincipalCollection principals,
Permission permission)
Ensures a subject/user Permission.implies(Permission) implies} the specified Permission. |
void |
checkPermission(PrincipalCollection principals,
String permission)
Ensures the corresponding Subject/user implies the specified permission String. |
void |
checkPermissions(PrincipalCollection principals,
Collection<Permission> permissions)
Ensures the corresponding Subject/user implies all of the
specified permission strings. |
void |
checkPermissions(PrincipalCollection principals,
String... permissions)
Ensures the corresponding Subject/user implies all of the
specified permission strings. |
void |
checkRole(PrincipalCollection principals,
String role)
Asserts the corresponding Subject/user has the specified role by returning quietly if they do or throwing an AuthorizationException if they do not. |
void |
checkRoles(PrincipalCollection principals,
Collection<String> roles)
Asserts the corresponding Subject/user has all of the specified roles by returning quietly if they do or throwing an AuthorizationException if they do not. |
void |
checkRoles(PrincipalCollection principals,
String... roles)
Same as checkRoles(PrincipalCollection subjectPrincipal, Collection<String> roleIdentifiers) but doesn't require a collection
as an argument. |
void |
destroy()
Destroys the cacheManager via LifecycleUtils.destroy. |
Authorizer |
getAuthorizer()
Returns the underlying wrapped Authorizer instance to which this SecurityManager implementation delegates all of its authorization calls. |
boolean |
hasAllRoles(PrincipalCollection principals,
Collection<String> roleIdentifiers)
Returns true if the corresponding Subject/user has all of the specified roles, false otherwise. |
boolean |
hasRole(PrincipalCollection principals,
String roleIdentifier)
Returns true if the corresponding Subject/user has the specified role, false otherwise. |
boolean[] |
hasRoles(PrincipalCollection principals,
List<String> roleIdentifiers)
Checks if the corresponding Subject/user has the specified roles, returning a boolean array indicating which roles are associated with the given subject. |
boolean[] |
isPermitted(PrincipalCollection principals,
List<Permission> permissions)
Checks if the corresponding Subject/user implies the given Permissions and returns a boolean array indicating which permissions are implied. |
boolean |
isPermitted(PrincipalCollection principals,
Permission permission)
Returns true if the corresponding subject/user is permitted to perform an action or access a resource summarized by the specified permission. |
boolean[] |
isPermitted(PrincipalCollection principals,
String... permissions)
Checks if the corresponding Subject implies the given permission strings and returns a boolean array indicating which permissions are implied. |
boolean |
isPermitted(PrincipalCollection principals,
String permissionString)
Returns true if the corresponding subject/user is permitted to perform an action or access a resource summarized by the specified permission string. |
boolean |
isPermittedAll(PrincipalCollection principals,
Collection<Permission> permissions)
Returns true if the corresponding Subject/user implies all of the specified permissions, false otherwise. |
boolean |
isPermittedAll(PrincipalCollection principals,
String... permissions)
Returns true if the corresponding Subject/user implies all of the specified permission strings, false otherwise. |
void |
setAuthorizer(Authorizer authorizer)
Sets the underlying Authorizer instance to which this SecurityManager implementation will delegate all of its authorization calls. |
| Methods inherited from class org.apache.shiro.mgt.AuthenticatingSecurityManager |
|---|
authenticate, getAuthenticator, setAuthenticator |
| Methods inherited from class org.apache.shiro.mgt.RealmSecurityManager |
|---|
afterCacheManagerSet, applyCacheManagerToRealms, getRealms, setRealm, setRealms |
| Methods inherited from class org.apache.shiro.mgt.CachingSecurityManager |
|---|
getCacheManager, setCacheManager |
| Methods inherited from class java.lang.Object |
|---|
clone, equals, finalize, getClass, hashCode, notify, notifyAll, toString, wait, wait, wait |
| Methods inherited from interface org.apache.shiro.mgt.SecurityManager |
|---|
createSubject, login, logout |
| Methods inherited from interface org.apache.shiro.session.mgt.SessionManager |
|---|
getSession, start |
| Constructor Detail |
|---|
public AuthorizingSecurityManager()
ModularRealmAuthorizer.
| Method Detail |
|---|
public Authorizer getAuthorizer()
public void setAuthorizer(Authorizer authorizer)
authorizer - the Authorizer this SecurityManager should wrap and delegate all of its
authorization calls to.protected void afterRealmsSet()
super.afterRealmsSet() and then sets these same Realm objects on this
instance's wrapped Authorizer.
The setting of realms the Authorizer will only occur if it is an instance of
ModularRealmAuthorizer, that is:
if ( this.authorizer instanceof ModularRealmAuthorizer ) {
((ModularRealmAuthorizer)this.authorizer).setRealms(realms);
}
afterRealmsSet in class AuthenticatingSecurityManagerpublic void destroy()
CachingSecurityManagercacheManager via LifecycleUtils.destroy.
destroy in interface Destroyabledestroy in class AuthenticatingSecurityManager
public boolean isPermitted(PrincipalCollection principals,
String permissionString)
AuthorizerThis is an overloaded method for the corresponding type-safe Permission variant.
Please see the class-level JavaDoc for more information on these String-based permission methods.
principals - the application-specific subject/user identifier.permissionString - the String representation of a Permission that is being checked.
Authorizer.isPermitted(PrincipalCollection principals,Permission permission)
public boolean isPermitted(PrincipalCollection principals,
Permission permission)
AuthorizerMore specifically, this method determines if any Permissions associated
with the subject imply the specified permission.
principals - the application-specific subject/user identifier.permission - the permission that is being checked.
public boolean[] isPermitted(PrincipalCollection principals,
String... permissions)
AuthorizerThis is an overloaded method for the corresponding type-safe Permission variant.
Please see the class-level JavaDoc for more information on these String-based permission methods.
principals - the application-specific subject/user identifier.permissions - the String representations of the Permissions that are being checked.
public boolean[] isPermitted(PrincipalCollection principals,
List<Permission> permissions)
AuthorizerMore specifically, this method should determine if each Permission in
the array is implied by permissions
already associated with the subject.
This is primarily a performance-enhancing method to help reduce the number of
Authorizer.isPermitted(org.apache.shiro.subject.PrincipalCollection, java.lang.String) invocations over the wire in client/server systems.
principals - the application-specific subject/user identifier.permissions - the permissions that are being checked.
public boolean isPermittedAll(PrincipalCollection principals,
String... permissions)
AuthorizerThis is an overloaded method for the corresponding type-safe Permission variant.
Please see the class-level JavaDoc for more information on these String-based permission methods.
principals - the application-specific subject/user identifier.permissions - the String representations of the Permissions that are being checked.
Authorizer.isPermittedAll(PrincipalCollection,Collection)
public boolean isPermittedAll(PrincipalCollection principals,
Collection<Permission> permissions)
AuthorizerMore specifically, this method determines if all of the given Permissions are
implied by permissions already associated with the subject.
principals - the application-specific subject/user identifier.permissions - the permissions to check.
public void checkPermission(PrincipalCollection principals,
String permission)
throws AuthorizationException
AuthorizerIf the subject's existing associated permissions do not Permission.implies(Permission) imply}
the given permission, an AuthorizationException will be thrown.
This is an overloaded method for the corresponding type-safe Permission variant.
Please see the class-level JavaDoc for more information on these String-based permission methods.
principals - the application-specific subject/user identifier.permission - the String representation of the Permission to check.
AuthorizationException - if the user does not have the permission.
public void checkPermission(PrincipalCollection principals,
Permission permission)
throws AuthorizationException
AuthorizerPermission.implies(Permission) implies} the specified Permission.
If the subject's exisiting associated permissions do not Permission.implies(Permission) imply}
the given permission, an AuthorizationException will be thrown.
principals - the application-specific subject/user identifier.permission - the Permission to check.
AuthorizationException - if the user does not have the permission.
public void checkPermissions(PrincipalCollection principals,
String... permissions)
throws AuthorizationException
Authorizerimplies all of the
specified permission strings.
If the subject's exisiting associated permissions do not
imply all of the given permissions,
an AuthorizationException will be thrown.
This is an overloaded method for the corresponding type-safe Permission variant.
Please see the class-level JavaDoc for more information on these String-based permission methods.
principals - the application-specific subject/user identifier.permissions - the string representations of Permissions to check.
AuthorizationException - if the user does not have all of the given permissions.
public void checkPermissions(PrincipalCollection principals,
Collection<Permission> permissions)
throws AuthorizationException
Authorizerimplies all of the
specified permission strings.
If the subject's exisiting associated permissions do not
imply all of the given permissions,
an AuthorizationException will be thrown.
principals - the application-specific subject/user identifier.permissions - the Permissions to check.
AuthorizationException - if the user does not have all of the given permissions.
public boolean hasRole(PrincipalCollection principals,
String roleIdentifier)
Authorizer
principals - the application-specific subject/user identifier.roleIdentifier - the application-specific role identifier (usually a role id or role name).
public boolean[] hasRoles(PrincipalCollection principals,
List<String> roleIdentifiers)
AuthorizerThis is primarily a performance-enhancing method to help reduce the number of
Authorizer.hasRole(org.apache.shiro.subject.PrincipalCollection, java.lang.String) invocations over the wire in client/server systems.
principals - the application-specific subject/user identifier.roleIdentifiers - the application-specific role identifiers to check (usually role ids or role names).
public boolean hasAllRoles(PrincipalCollection principals,
Collection<String> roleIdentifiers)
Authorizer
principals - the application-specific subject/user identifier.roleIdentifiers - the application-specific role identifiers to check (usually role ids or role names).
public void checkRole(PrincipalCollection principals,
String role)
throws AuthorizationException
AuthorizerAuthorizationException if they do not.
principals - the application-specific subject/user identifier.role - the application-specific role identifier (usually a role id or role name ).
AuthorizationException - if the user does not have the role.
public void checkRoles(PrincipalCollection principals,
Collection<String> roles)
throws AuthorizationException
AuthorizerAuthorizationException if they do not.
principals - the application-specific subject/user identifier.roles - the application-specific role identifiers to check (usually role ids or role names).
AuthorizationException - if the user does not have all of the specified roles.
public void checkRoles(PrincipalCollection principals,
String... roles)
throws AuthorizationException
AuthorizercheckRoles(PrincipalCollection subjectPrincipal, Collection<String> roleIdentifiers) but doesn't require a collection
as an argument.
Asserts the corresponding Subject/user has all of the specified roles by returning quietly if they do or
throwing an AuthorizationException if they do not.
principals - the application-specific subject/user identifier.roles - the application-specific role identifiers to check (usually role ids or role names).
AuthorizationException - if the user does not have all of the specified roles.
|
||||||||||
| PREV CLASS NEXT CLASS | FRAMES NO FRAMES | |||||||||
| SUMMARY: NESTED | FIELD | CONSTR | METHOD | DETAIL: FIELD | CONSTR | METHOD | |||||||||